×
![Enlarged Image]()
Understanding And Preparing For Cyber Threats To Uncrewed Vehicle Systems
- Connected and automated technologies in ground vehicles present opportunities for efficiency and safety but introduce heightened risks of cyber threats.
- Autonomous ground vehicles (AGVs) are a unique blend of mobile-computing,
enterprise systems, and control systems with
- unique challenges for cybersecurity,
- combination of cyber and physical systems,
- higher transportation costs.
- Cyber-physical simulation can help us understand emerging cyber-threats to ground vehicles and how their systems can be affected, including the physical response of vehicles to cyber-attack.
Key Partners
MSU Center for Advanced Vehicular Systems
MSU Center for Cyber Innovation
MSU Raspet Flight Research Labs
University of Colorado Boulder
Circadence
Neya Systems
MartinFed
University of Michigan
US Army Automotive Research Center
US Army DEVCOM Ground Vehicle Systems Center
US Army PEO STRI Threat Systems Management Office
Objective
By partnering with centers, academic institutions, industry collaborators, and government agencies, CAVS is working to develop and leverage physical and virtual test platforms to investigate vulnerabilities of autonomous ground vehicle systems to cyber-threats:
- Extending the Netmapper/Cyber Range Automation Framework to provide a scalable hybrid cyber-range modeling and simulation environment for discovering, evaluating, and/or developing mitigation strategies for cyber-vulnerabilities in robotic and uncrewed autonomous systems (R/UAS).
- Evaluating multiple military-relevant autonomy stacks, develop automated cyber agents, investigate intuitive UI for alerting operators to cyber threats, and robustly handle capability degradation as a result of attacks.
- Investigating techniques to detect attacks on vehicle sensors, diagnose the effects of the attack, and help soldier operators effectively respond to the attack.
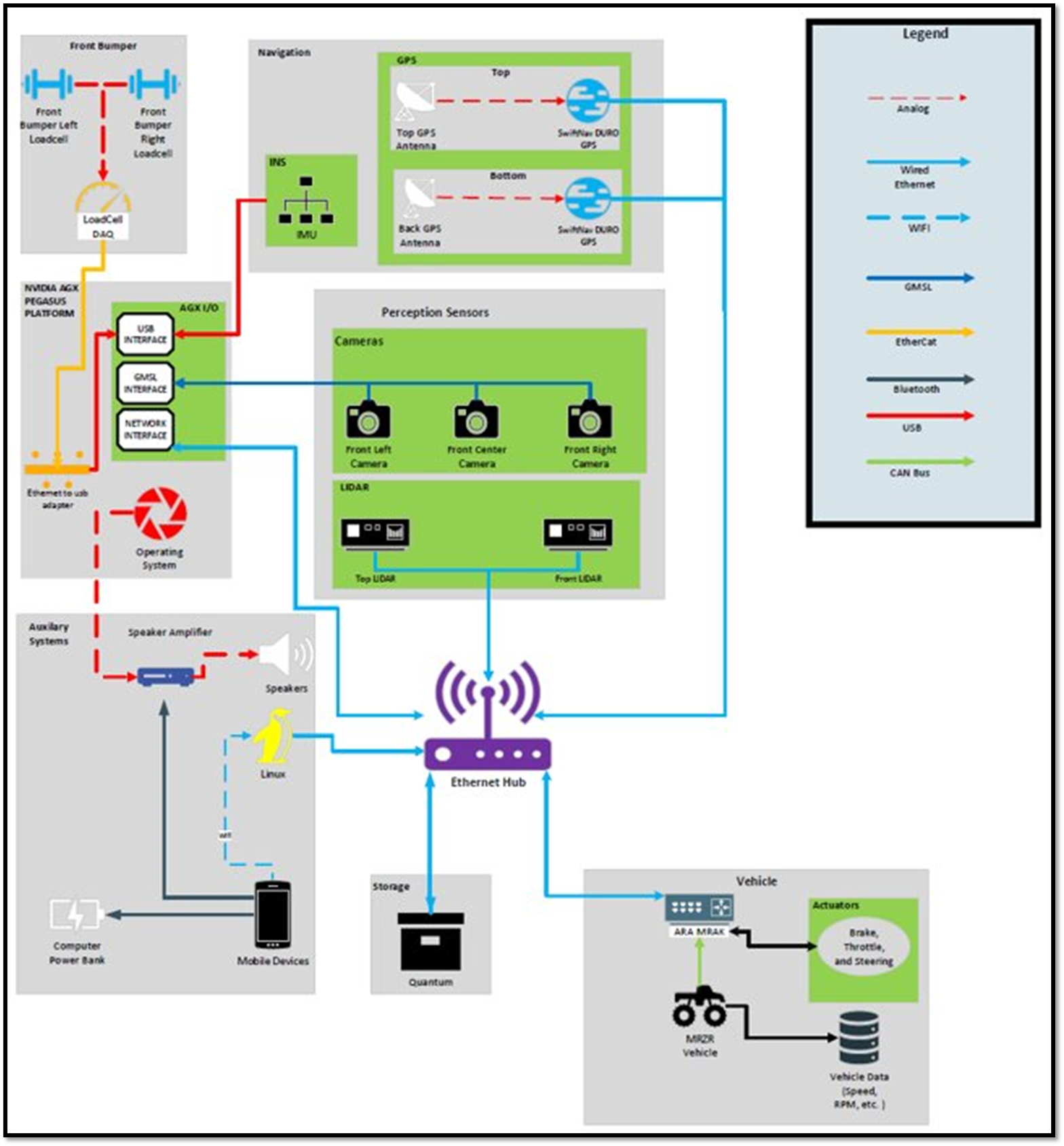

Outcomes
- Assessment of Application of Tactics, Techniques, and Procedures (TTPs) to R/UAS
- Catalog of R/UAS Components and Associated Cyber-vulnerabilities
- Interactive Simulations of Cyber-Physical Systems and Effects of Cyber Attacks
- Intuitive User Interfaces Designed to Support Effective Soldier Action

